Footprinting and it’s techniques
Before starting with the content, let me connect footprinting with real life scenario so that it can help you understand the actual concept behind the word “Footprinting”. For that let us take an example of a movie, if you have seen any action movie related with bank robbery , do the characters directly buy guns and masks and enter the bank to rob it? No! If they did this, they wouldn’t be able to rob the bank successfully. High chances are they won’t even be able to figure out the way to the safe.
Before going to rob the bank, what they do is make proper plan which includes collecting information about the entrance way of the bank, safe where the money is kept, how to bypass the security system, which areas has less security and escape way of the bank without being tracked. As you can see, knowing about the bank plays an important role here.
Likewise, if you are an ethical hacker or someone who is trying to explore the vulnerabilities of any given site, you need to know about your target very well before manipulating what’s inside. You need to have certain information about your target, which is known as Footprinting. This is also considered as the first step, if you are trying to persuade your career as a penetration tester.
Technical Definition of Footprinting
Footprinting is basically a process of finding all the possible ways to intrude into a target system or at least decide what type of attacks will be more suitable for the target
Types of Footprinting
There are two types of footprinting:
- Active Footprinting:
Active Footprinting is a process of collecting information by directly communicating with the concerned personal or the machine.
2. Passive Footprinting:
Passive Footprinting is a process of gathering information about any victim without any direct communication. This can be done using various google search or public reports.
How can footprinting help attackers?
- Footprinting helps attacker to know about the security posture of target organization.
- It helps attacker reduce their focus area to specific range of IP address, networks, domain ranges etc.
- It can also benefit attacker by helping them select appropriate exploits by allowing attacker to identify vulnerabilities in the target systems.
- It can allow attackers to draw a network map or outline the target organization’s network infrastructure to know about the actual environment that they are going to break.
Ways and Tools for Footprinting any target
Now, let us look forward on how can Footprinting be done with various methods and available tools.
- Search:
It all starts from our browsers. Everything you need is available on the Internet. Let us suppose we are trying to gather information about Cisco. All you need to do is, go to your browser and enter “Cisco”. You will now get the url, which is the first piece of information you have.
Not just limiting to url but, proper search can also help attacker to extract information about a target such as technology platforms, employee details, login pages, intranet portals, etc. which helps in performing social engineering and other types of advanced system attacks.
ping target.com
Now, you can see that we have the information about the Ip of the target domain.
3. Whois Lookup:
ping target.com
Now, you can see that we have the information about the Ip of the target domain.
3. Whois Lookup:
This tool simply gives answer to the question, “What is that Website?”. It can gather informations such as Platform, Type of script, Google Analytics, Web Server Platform, Ip Address, Country, Server Headers, Cookies and lot more. You can simply type the following command in your linux console:
whois target.com7. p0f:
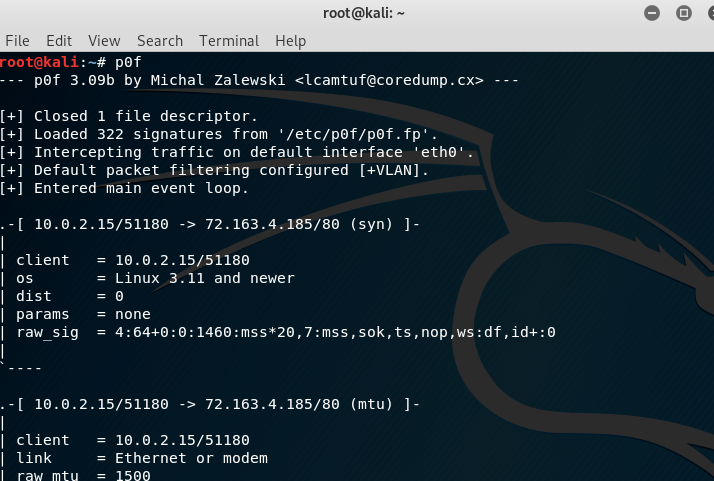
It is a technique that analyzes the structure of TCP/IP packet to determine the operating system and other configuration property of a remote host. p0f is basically a forensic tool, which can also be used while doing forensics on a compromised system or a system under attack. Steps to run p0f:
i. On linux terminal, enter p0f
ii. Open your target host in any browser and start exploring it.
Once, the connection is established, client will start to interact with the server.
In the above screenshot, you can see my client ip [10.0.2.15] Established a Connection with Target web server [72.163.4.185] with port number 80.
8. Recon-ng:
Recon-ng, tool written in Python is specially used for information gathering with its independent modules, keys list and other modules.
Now let’s try using one the modules that does not require an API key. There are many, but let’s use one for scanning for XSS (cross-site scripting) vulnerabilities called XSSposed.
i. Simply type recon-ng in your linux command line or Go to Application-Information Gathering- recon ng.
ii. For help regarding the tool, you can simply enter:
recon-ng > help- You can find details about the other available modules by the following command:
recon-ng > show modulesiii. Now, we need to load the module:
recon-ng > use recon/domains-vulnerabilities/xssposed- To get more info about the module:
recon-ng > show infoiv. As you can see above, the only option we need is the website we want to scan. Let us scan microsoft.com. For that we need to set the source.
recon-ng > set SOURCE microsoft.comv. Then tell Recon-ng to run:
recon-ng > run
In the above screenshot, you can see list of known XSS vulnerabilities reported of microsoft.com so far along with the link to the report and it’s status
9. Google Dork:
Query string can be used in search and can be used as keywords. Also Google Advance Search Operators can be utilized in order to gather information about the target host. For further information regarding google dork, you can click the link here.
You can also refer to Google Hacking Database (GHD) to explore different search terms that have been found to reveal sensitive data exposed by vulnerable servers and web applications.
10. Nikto:
Nikto is a Web Server Scanner that tests for dangerous files and outdated service software, whose details can be exploited and used to hack the network. These results can be utilized to understand the weaknesses of the network or application according to which you can choose relevant attacks to hack the network.
i. In order to run Nikto, on your Kali Linux Terminal, enter nikto.
ii. To know about the different command, you can simply open help file:
nikto -helpiii. Now, to scan your target host:
nikto -h targetIP Here, -h indicates the host. Now, let us try for microsoft.com and see what we can get as a result

You can also store the results in your Desktop by using the following command:
nikto -h targetc.com -o nikto_results -F txtHere, -o indicates Output and -F indicates the file type, which in our case we have given as txt. Hit enter and now you can see the result txt file saved on your desktop.
Footprinting Counter Measures
Here are some of the counter measures you can take to avoid attackers to footprint anything that is associated with your organization.
- Configure routers to restrict the responses to footprinting requests.
- Use firewalls to block the ports in order to prevent un-authorized port scans.
- Publish exactly what you want to publish and nothing more.
- Prevent search engines from caching a web page.
- Use anonymous registration services.
- Configure web services to avoid information leakage.
- Disable unwanted protocols.
- Use IDs that can be configured to refuse suspicious traffic and pick up footprinting pattern.
- Create security policies to regulate information that employees can reveal to third parties.
- Keep internal DNS and external DNS separate.
- Educate your employees about social engineering tricks and risks.
- Restrict unexpected inputs by keeping proper validations in forms where user input is taken
- Encrypt and password protect critical information.
- Always use TCP/IP and IPSec protocols.
- Configure IIS against banner grabbing
Conclusion: At first, gathering information might be very boring process and time consuming process, but remember that it is very important to know about your target before you conduct any attack as a penetration tester. Next, we will discuss about the second important step of penetration testing, which is also known as “Scanning”.